OpenDoH
https://dns.opendoh.com/dns-query
https://adblock.opendoh.com/dns-queryDefault: https://dns.opendoh.com/dns-query
The “Default” servers provide a secure and reliable connection, but they don’t filter anything.
Adblock: https://adblock.opendoh.com/dns-query
These servers block ads, tracking, and phishing.
Why DNS over HTTPS (DoH)?
DNS serves as the Internet’s phonebook, converting human-readable domain names into machine-readable IP addresses. By default, DNS queries and responses are transmitted in plaintext using UDP, making them susceptible to interception by networks, ISPs, or anyone with the ability to monitor transmissions. Even if a website employs HTTPS for secure communication, the DNS query essential for accessing that site remains exposed.
The absence of privacy in DNS has significant implications for security and, in certain instances, human rights. When DNS queries lack privacy, it becomes simpler for governments to enforce Internet censorship and for attackers to surveil users’ online activities.
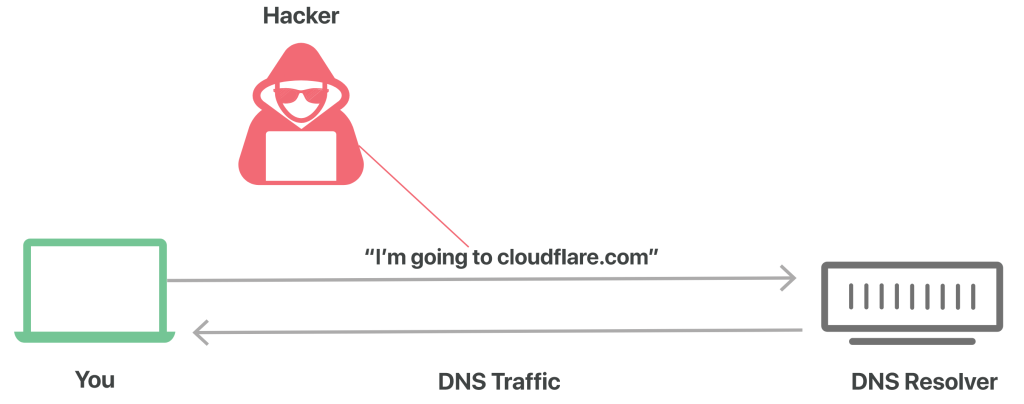
Consider a regular, unencrypted DNS query as analogous to a postcard sent through the mail: anyone handling the mail might catch a glimpse of the text on the back, making it unwise to send sensitive or private information on a postcard.
DNS over HTTPS are two standards designed to encrypt plaintext DNS traffic, preventing malicious entities, advertisers, ISPs, and others from interpreting the data. To extend the analogy, these standards aim to encase all postcards in an envelope before sending them through the mail. This way, individuals can send postcards without worrying that someone might be snooping on their activities.
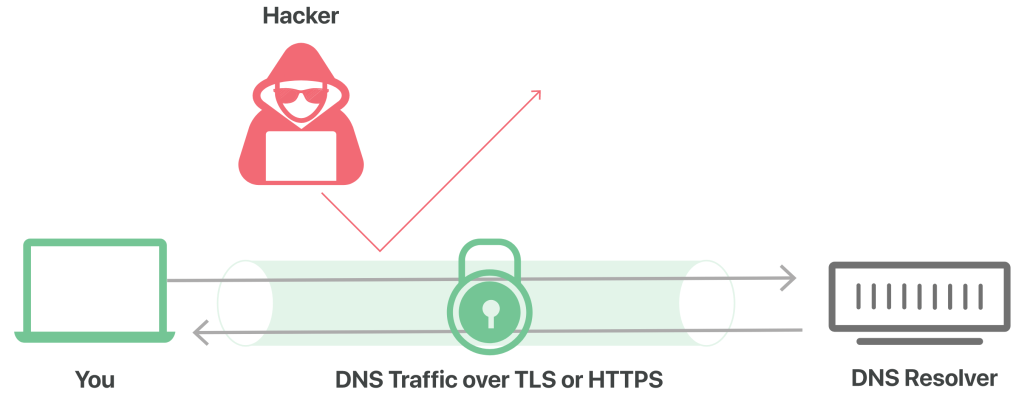
DNS over HTTPS, abbreviated as DoH, serves as an alternative to DNS over TLS (DoT). In DoH, DNS queries and responses undergo encryption, but they are transmitted through the HTTP or HTTP/2 protocols instead of directly using UDP. Similar to DoT, DoH ensures that attackers cannot forge or tamper with DNS traffic. From the perspective of a network administrator, DoH traffic resembles other HTTPS traffic, such as typical user interactions with websites and web applications.
Which is better, DoT or DoH?
This is up for debate. DoT gives network administrators the ability to monitor and block DNS queries, which is important for identifying and stopping malicious traffic. DoH queries, meanwhile, are hidden in regular HTTPS traffic, meaning they cannot easily be blocked without blocking all other HTTPS traffic as well.
From a privacy perspective, DoH is arguably preferable. With DoH, DNS queries are hidden within the larger flow of HTTPS traffic. This gives network administrators less visibility but provides users with more privacy.
https://dns.opendoh.com/dns-query
https://adblock.opendoh.com/dns-queryConfigure DoH
There are several browsers and devices compatible with DNS over HTTPS (DoH). This protocol lets you encrypt your connection to OpenDoH in order to protect your DNS queries from privacy intrusions and tampering.
Mozilla Firefox
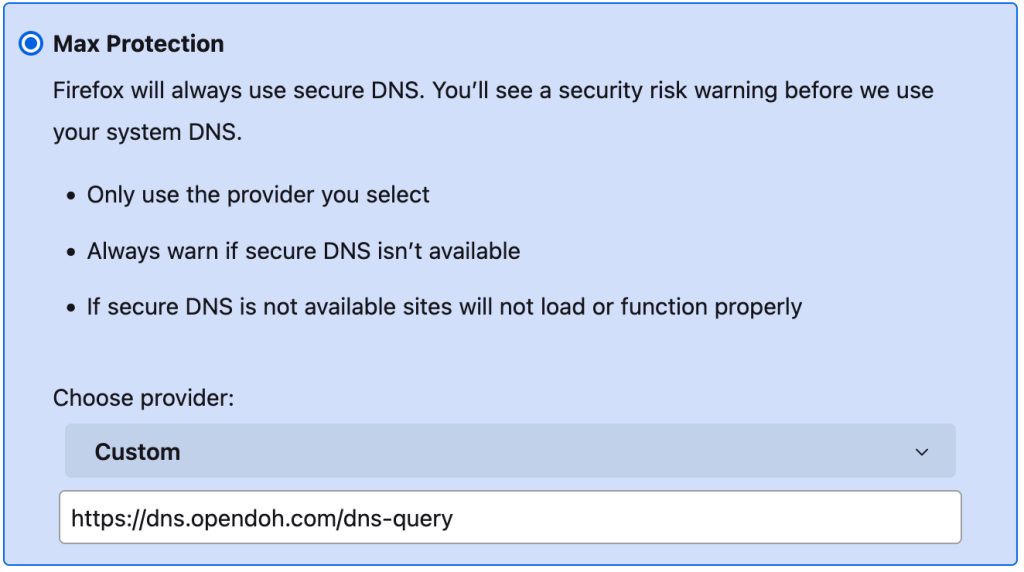
- Select the menu button > Settings.
- In the Privacy & Security menu, scroll down to the Enable secure DNS using: section.
- Select Increased Protection or Max Protection.
- Select With Custom and use OpenDoH URL.
Google Chrome
- Select the three-dot menu in your browser > Settings.
- Select Privacy and security > Security.
- Scroll down and enable Use secure DNS.
- Select the With option, and from the drop-down menu use OpenDoH URL.
Microsoft Edge
- Select the three-dot menu in your browser > Settings.
- Select Privacy, Search, and Services, and scroll down to Security.
- Enable Use secure DNS.
- Select Choose a service provider.
- Select the Enter custom provider drop-down menu and use OpenDoH URL.
Brave
- Select the menu button in your browser > Settings.
- Select Security and Privacy > Security.
- Enable Use secure DNS.
- Select With Custom and use OpenDoH URL.
iOS
On an iOS device you can download special ‘.mobileconfig’ file that adds DNS-over-HTTPS servers to the DNS settings.
macOS
On an macOS device you can download special ‘.mobileconfig’ file that adds DNS-over-HTTPS servers to the DNS settings.
“The first step for your privacy on the internet.”
